Quite a long title for quite an annoying issue. Let me explain the set-up first: I have pipelines running in Azure Data Factory and I want to send e-mails with customized messages when something goes wrong (this means the standard alerting of ADF doesn’t cut it). ADF doesn’t have a built-in activity for sending e-mails (yes, I know, it’s 2024 and this is still lacking, but Fabric has it). First I used an Azure Logic App to do this, but there you need to log into Office 365 with an actual user, and I’m not really keen that my user account would be used in an automated process. So I switched to an Azure Function where I use PowerShell to send an e-mail using the Microsoft Graph AI SendMail endpoint. To authenticate, I’m using an app registration that has the Mail.Send permission assigned to it.
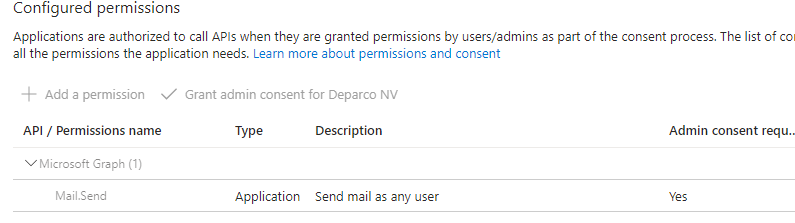
The secret of this app registration is stored in Azure Key Vault and the Azure Function app retrieves this as part of the application settings.
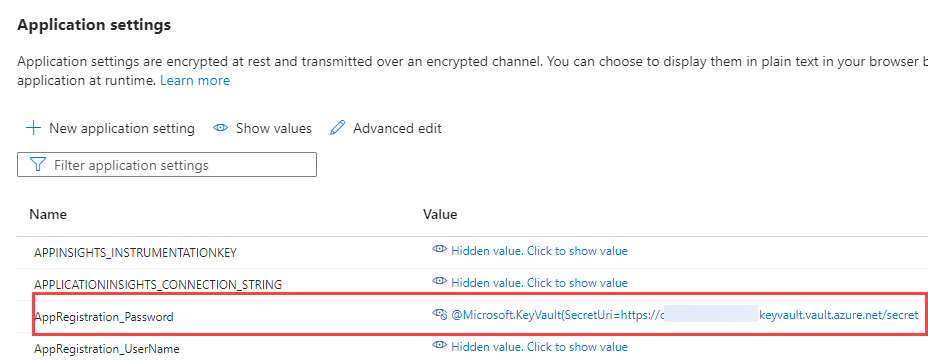
In the PowerShell function, this application setting is retrieved as an environment variable so it can authenticate with the Graph API using the app registation. So far so good, except that the secret of this app registration expires after 1 year (some time ago you could configure an expiration date for in the future, but it seems this isn’t possible anymore). The Azure Function started crashing with a 401 (Unauthorized) error.
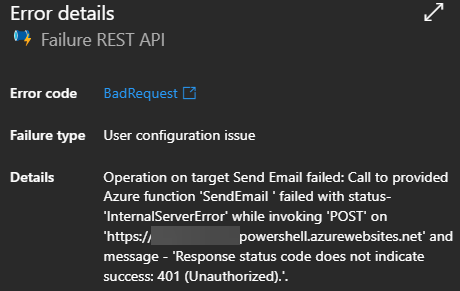
Naively, I thought that adding a new version to the Azure Key Vault secret that stores the app registration secret would fix the issue. Alas, the same error was returned. I disabled the older version in Azure Key Vault. Still the same error. I restarted the Azure Function app. You guessed it: the same error. Apparently, the Function App caches the value of the application setting and very stubbornly it doesn’t reread it when restarted (even when stopped and then started). This is a known issue, but unlike what someone suggested, breaking the configuration and then fixing it again didn’t flush the cache.
The only reliable method to get the new Key Vault version is waiting 24 hours. After a certain time period, it seems the cache is invalidated and the new value is fetched. Another method that might work but requires some work is deleting the configuration and creating a new one – with a different name – but this means you’ll need to update the Azure Function itself as well. If you know of any other methods, let me know in the comments.
UPDATE 1: it’s an option to explicitly specify a version of the Key Vault secret in the app configuration. However, I want to avoid this as you would need to update the configuration each time the token expires. When you don’t specify a version, the app configuration should take the latest version, so in an ideal world where this caching bug doesn’t exist, not specifying a version is the preferred solution.
UPDATE 2: another option is suggested by Bartosz:
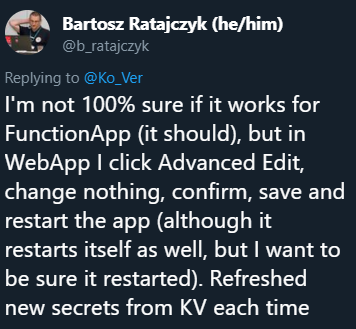
The Advanced Edit can be found here:
I haven’t tested it myself though. Maybe next year when the secret expires again 🙂
------------------------------------------------
Do you like this blog post? You can thank me by buying me a beer 🙂